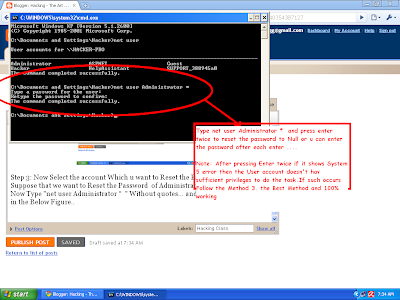
When a hard drive crash or media failure happens, knowledgeable and prudent professionals call to us more than any other company to salvage their seemingly unrecoverable data.
Data suddenly disappeared, you can not access the data, computer will not boot, hard disk is not recognized and data problems arise when you are first checkpoint .
Type of Recovery
The logical processing task to rebuild the system and data processing work on the structure of the physical damage to the hard disk. It is highly difficult task requiring both skill and experience, if a physical failure, we also work other logical processes. So yes, a measure of the state of the art data recovery disaster recovery rate of the physical.Hard Disk Drive (HDD; Hard Disk Drive) is a high speed rotating disk coated with magnetic material, by moving the magnetic head reads the information recorded, the typical data storage devices are. Mainly personal computers, servers, RAID configuration NAS (Terastation, LANDISK) has been used by others. Recently, hdd recorder / HDD video , iPod, PS3, we have introduced a wide range of digital devices ranging from mobile phones in general. Recently, new technology, weak magnetic shocks, and structural weaknesses and limitations of mechanical disk SSD (Solid-state Drive) has received much attention.
Type of Hard Disk Drives
IDE Integrated/Intelligent Drive/Device Electronics. First appeared years ago, hard 50 "RAMAC" was not a huge 24inch stacked disks 50. The hard disk, now took the form of, IDE hard disk is. Hard and ST-506 MFM, RLL and IDE becomes the EIDE, Ultra ATA went on to develop.
However, cable can not solve the problem of noise during data transmission, Serial ATA will change to look like.SAS is one of the SCSI standard, whereas previous SCSI parallel transmission standards, SAS provides a serial transmission and they, in terms of speed is more than four times faster. In addition, 50% lower power consumption can be reduced by at least a high performance, high availability can be demonstrated.
External hard Disk
External hard drive (HDD), you have excellent phone, data and video and music recording and data backup large amounts of information is growing rapidly in demand. Primarily on the USB interface is used, IEEE (Firewire), eSATA, LAN and Internet connections available methods are also used. Convenient to carry the portable HDD, RAID configuration recently, NAS has been released from products that meet the diverse needs of products supported.
Common failures of the external hard drive content
Suddenly no longer recognizes.I can hear noise from the hard drive.
" Safely Remove Hardware "message is displayed, OS does not recognize the drive.
" USB device not recognized "message.
" is not formatted. Do you want to format? "In the message. File system damage-PBS, FAT, MFT ERR
" delayed write error "message.
" Drive not accessible "message.
Device Manager "!" And "?" Mark out.
I do not know the meaning of the text is displayed. ( recovery rate of 90% or more )
0 is a disk size information to determine Disc.
Common disorder mostly external hard disk, MBR is damaged or if you fall, PBS partition configuration information (Partition Boot Sector ) or FAT (File Allocation Table) and if it is damaged it.